This post will be about the reversing serialized objects, located in ORB file.They are written in ORB using MFC library.
Firstly, I parsed class names. To do that, I have written simple program in C++. Each class in Pink starts with letter ‘C’, so program just finds this letter, then reads name as MFC String and checks it for correctness.
I’ve got 48 for Peril and 45 for Pokus.
Secondly, I found out fields names. It was really easy.
When these games were created, developers had program creating the game files. This program wrote data to txt files, but not using MFC serialization, because the game engine has code for executing game from txt files. That’s why each class has virtual method, which writes attribute name and value. For example, CConditionVariable class:
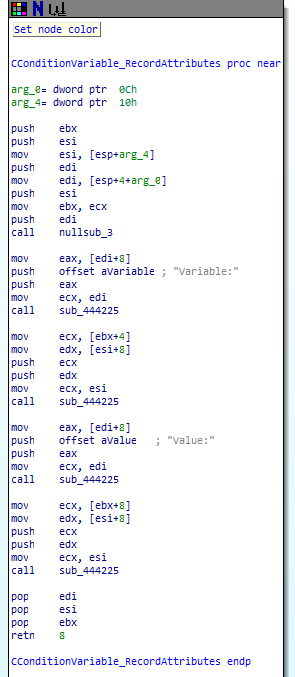
Each class in Pink games can be reversed using this approach.